
December 05, 2022
Dipsy Kapoor
|
SearchStax is proud to announce the winners of the 2022 Partner Excellence Award. The annual Partner Excellence Award showcases innovative digital transformations that SearchStax’s partners achieve for their clients and the overall strategic importance of alliances.
Apache Calcite has a vulnerability, CVE-2022-39135, that is exploitable in Apache Solr in SolrCloud mode. If an untrusted user can supply SQL queries to Solr’s “/sql” handler (even indirectly via proxies / other apps), then the user could perform an XML External Entity (XXE) attack.
An XXE attack may lead to the disclosure of confidential data, denial of service, server-side request forgery (SSRF), port scanning from the Solr node, and other system impacts.
Apache Solr versions 6.5 to 8.11.2 are affected by this vulnerability.
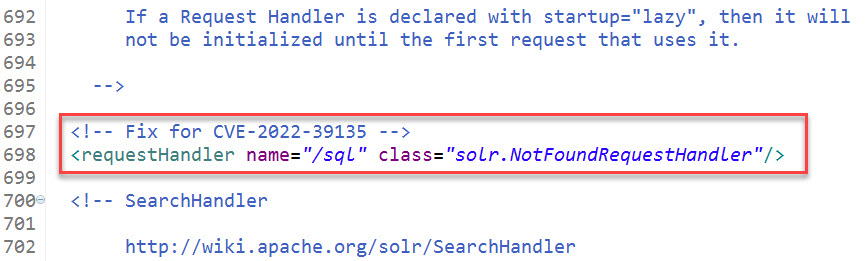
As recommended by the Apache Solr website, any of the following steps should help prevent this vulnerability from being exploited in your Solr deployment:
<requestHandler name="/sql" class="solr.NotFoundRequestHandler"/>
We recommend adding this configuration just before the SearchHandler section around line 697. (Your line numbers may differ.)
SearchStax Cloud provides Cloud Private environments, IP Filtering, and Basic Authentication to secure your deployments and recommends using these Security settings whenever possible.
If you have any other questions about the Solr Vulnerability, please contact SearchStax Support or submit a support ticket.
Copyrights © SearchStax Inc.2014-2024. All Rights Reserved.
close
close
close